How to manage multiple http and https servers
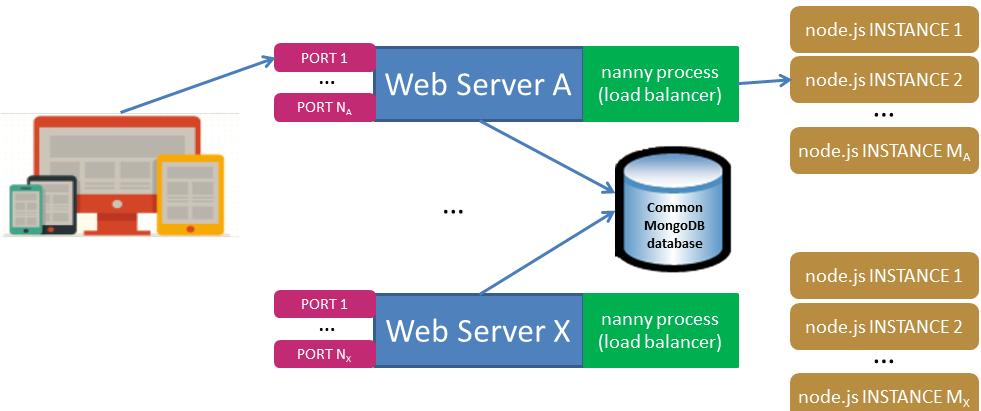
Sage X3 version V11 web platform is able to run on multiple web servers. Every web server can handle several node.js instances, which are managed by a load balancer (a dedicated nanny process handles the load balancer).
A web server can be accessible on several ports. The set up for each port can be different (for example, a port can be on http or https for instance).
All web servers will connect to the same repository if they share the same MongoDB instance. The set up of the different servers is defined by the host entity.
The following schema summarizes the architecture:

Every server S can have Ns ports and manage Ms node instances.
If a server is dedicated to the web server layer, at least one node.js process (and probably more) should run per processor core (recommendations for memory and number of node processes per core will be published soon).
When a direct exposition on the web is necessary:
It is possible to have both http and https connections on two different ports of the same server.
When installing on a web server, be aware of the following:
To run in https:
Remark (when you buy a certificate): At the moment, private keys in PKCS #1 and PKCS#8 formats are accepted (in PEM format, not DER format), either unencrypted or with traditional SSLeay compatible encryption (at PEM level; supported encryptiong mechanisms: DES-EDE3-CBC and DES-CBC, that is: DES and triple-DES). The encryption at ASN.1 level is not yet supported.
In other words: When you have a private key in PEM format and the first line of the file contains -----BEGIN PRIVATE KEY----- or -----BEGIN RSA PRIVATE KEY----- it is OK, but when it contains -----BEGIN ENCRYPTED PRIVATE KEY----- it is not OK.
Conversion between the formats can be done using openssl (or other tools).
Example: Converting a private key in PKCS #8 format with encryption into a format which can be handled (on Microsoft Windows):
openssl pkcs8 -in privatekey1 -out tempfile
openssl rsa -in tempfile -des3 -out privatekey2
del tempfile