Documentation
Personal data: list, content and location
The standard data types associated with personal data main records:
|
Data type |
Description |
|---|---|
|
AIN |
Contact (relationship) |
|
AUS |
User |
|
BID |
Bank account number |
|
BPA |
Address |
|
BPC |
Customer |
|
BPR |
Business partner |
|
BPS |
Supplier |
|
BPT |
Carrier |
|
COR |
Outlook contact |
|
E164TEL, TEL, TELTC |
Phone numbers/fax numbers |
|
FNA |
First name |
|
GAC |
Account (general or individual) |
|
LDS |
Lead |
|
MAI |
Email address |
|
NAM |
Names |
|
REP |
Sales representative |
The detail of the personal data looks as follows:
|
Table |
Description |
Description |
Field |
|---|---|---|---|
|
BAPPOINT |
Appointment |
BP |
APTCMP |
|
Contact to visit |
APTCCNNUM |
||
|
Outlook contact |
APTCOR |
||
|
Sales rep |
APTREPNUM |
||
|
Recording |
APTRECADD |
||
|
Telephone |
APTTEL |
||
|
Mobile phone |
APTMOB |
||
|
Email address |
APTEML |
||
|
Organizer |
ATPREPMNA |
||
|
BID |
Bank details |
Entity |
BPANUM |
|
Bank account number |
BIDNUM |
||
|
BILLLADH |
Bill of lading header |
BP |
BPR |
|
Ship-to customer |
BPRNAM |
||
|
Carrier |
BPTNUM |
||
|
BP1096PRN |
1096 print table |
Telephone |
TEL |
|
Fax |
FAX |
||
|
BP1099BEGBAL |
1099 beginning balance |
Supplier |
BPSNUM |
|
BP1099PRN |
1099 print table |
Supplier |
BPSNUM |
|
Telephone |
TEL |
||
|
BPADDRESS |
Addresses |
Entity |
BPANUM |
|
By default |
BPABID |
||
|
Telephone |
TEL |
||
|
Fax |
FAX |
||
|
Mobile phone |
MOB |
||
|
Internet address |
WEB |
||
|
BPARTNER |
Business partner |
BP |
BPRNUM |
|
Company name |
BPRNAM |
||
|
Default contact |
CNTNAM |
||
|
Default bank account number |
BIDNUM |
||
|
Partner |
CSLBPR |
||
|
BPCARRIER |
Carriers |
Carrier |
BPTNUM |
|
Company name |
BPTNAM |
||
|
Default contact |
CNTNAM |
||
|
BPCCATEG |
Customer category |
Sales rep |
REP |
|
Sales rep |
REPDLV |
||
|
Carrier |
BPTNUM |
||
|
BPCUSTMVT |
Customer transactions |
Customer |
BPCNUM |
|
Risk BP |
BPCRSK |
||
|
BPCUSTOMER |
Customers |
Customer |
BPCNUM |
|
Company name |
BPCNAM |
||
|
Bill-to customer |
BPCINV |
||
|
Pay-by customer |
BPCPYR |
||
|
Group customer |
BPCGRU |
||
|
Risk customer |
BPCRSK |
||
|
Default contact |
CNTNAM |
||
|
Sales rep |
REP |
||
|
Insurance company |
BPCCDTISR |
||
|
Contact |
CNTEFAT |
||
|
BPDLVCUST |
Ship-to customer |
Customer |
BPCNUM |
|
Company name |
BPDNAM |
||
|
Carrier |
BPTNUM |
||
|
Freight agent |
FFWNUM |
||
|
Sales rep |
REP |
||
|
BPEXCEPT |
BP-Company exception |
BP |
BPRNUM |
|
BPMISC |
Order-giver/miscellaneous BP |
BP code |
BPRNUM |
|
BPS1099GEN |
1099 generation |
Supplier |
BPSNUM |
|
BPS1099MNT |
Supplier 1099 maintenance |
Supplier |
BPSNUM |
|
BPS1099PAY |
Supplier 1099 payments |
Supplier |
BPSNUM |
|
BPSCATEG |
Supplier category |
Carrier |
BPTNUM |
|
Freight agent |
FFWNUM |
||
|
BPSHISUPLN |
Ship-to addresses |
Supplier |
BPSNUM |
|
Shipping supp. |
BPSSHI |
||
|
BPSHISUPP |
Shipping site suppliers |
Shipping supp. |
BPSSHI |
|
Company name |
BPSNAM |
||
|
Freight agent |
FFWNUM |
||
|
BPSUPPLIER |
Suppliers |
Supplier |
BPSNUM |
|
Company name |
BPSNAM |
||
|
Pay-to |
BPRPAY |
||
|
Supplier invoice |
BPSINV |
||
|
Supplier group |
BPSGRU |
||
|
Risk BP |
BPSRSK |
||
|
Carrier |
BPTNUM |
||
|
Default contact |
CNTNAM |
||
|
BPSUPPMVT |
Supplier transactions |
Supplier |
BPSNUM |
|
Risk BP |
BPSRSK |
||
|
BSIDUD |
Open items |
Bill-to/Order BP |
BPR |
|
Pay-by |
BPRPAY |
||
|
BSIIMPPAR |
Bank import settings |
Account |
ACCSUSPENSE |
|
From BP |
BPRSTR |
||
|
To BP |
BPREND |
||
|
CALLATTEMP |
Call attempt |
Company |
CTTCMP |
|
Contact (relationship) |
CTTCCN |
||
|
Sales rep |
CTTREP |
||
|
CARAREA |
Carrier regions |
Carrier |
BPTNUM |
|
CARPRICE |
Carrier price lists |
Carrier |
BPTNUM |
|
CASHPAYSPA |
Cash payments |
BP code |
BPRNUM |
|
CBNDET |
MRP detail |
Source BP |
BPRNUM |
|
CCMCRORIGC |
Customer originators |
Customer |
BPCNUM |
|
Contact |
CUSTCONTACT |
||
|
CCMCRORIGE |
External originators |
Contact |
EXTCONTACT |
|
CCMCRORIGS |
Supplier originators |
Supplier |
BPSNUM |
|
Contact |
SUPPCONTACT |
||
|
CCMIMPMFGD |
Impact analysis-Work orders |
Ship-to customer |
BPCNUM |
|
CCMIMPPOD |
Impact analysis-Purchases |
Supplier |
BPSNUM |
|
CCMIMPPRD |
Impact analysis-Purchase req |
Supplier |
BPSNUM |
|
CCMIMPSCD |
Impact analysis-Subcontract |
Supplier |
BPRNUM |
|
CCMIMPSOD |
Impact analysis-Sales orders |
Sold-to |
BPCORD |
|
CCMIMPSQD |
Impact analysis-Sales quotes |
Sold-to |
BPCORD |
|
CFGHISHEA |
Configuration history header |
BP |
CFGBPRNUM |
|
CFGMEMO |
Configurator memo |
BP |
CFGBPRNUM |
|
CFODUDDATE |
Cash forecast management |
Bill-to/Order BP |
BPR |
|
Pay-by |
BPRPAY |
||
|
CFOMANMVT |
Cash forecast movements |
BP |
BPRNUM |
|
COMPANY |
Company |
Company name |
CPYNAM |
|
Contact |
CNTNAM |
||
|
Bank account number |
BIDNUM |
||
|
Tax center |
GERTAXCEN |
||
|
COMREP |
Sales rep commissions |
Sales rep |
REP |
|
CONCESSION |
Concession |
Grantor |
CCNUSR |
|
CONTACT |
Contacts |
Entity |
BPANUM |
|
Contact code |
CCNCRM |
||
|
Telephone |
TEL |
||
|
Fax |
FAX |
||
|
|
WEB |
||
|
Mobile phone |
MOB |
||
|
CONTACTCRM |
Contact relationships |
Code |
CNTNUM |
|
Last name |
CNTLNA |
||
|
Telephone |
CNTETS |
||
|
Fax |
CNTFAX |
||
|
Mobile phone |
CNTMOB |
||
|
|
CNTEMA |
||
|
CONTAINER |
Container |
Supplier |
BPSNUM |
|
CONTCOV |
Service contracts coverage |
Customer |
BPC |
|
CONTSERV |
Service contract |
Sold-to |
CONBPC |
|
Bill-to customer |
CONBPCINV |
||
|
Pay-by |
CONBPCPYR |
||
|
Group customer |
CONBPCGRU |
||
|
Contact (relationship) |
CONCCN |
||
|
Sales rep |
SALREP |
||
|
CONTSERVX |
Sold-to |
CONBPC |
|
|
Bill-to customer |
CONBPCINV |
||
|
Pay-by |
CONBPCPYR |
||
|
Group customer |
CONBPCGRU |
||
|
Contact (relationship) |
CONCCN |
||
|
Sales rep |
SALREP |
||
|
CORREP |
Representative in charge |
Sales rep code |
COPREP |
|
CORRESPOND |
Outlook contact |
Last name |
LNA |
|
First name |
FNA |
||
|
|
HOMEML |
||
|
Telephone |
HOMTEL |
||
|
Fax |
HOMFAX |
||
|
Mobile phone |
HOMMOB |
||
|
Code |
CNTNUM |
||
|
BP |
BPRNUM |
||
|
|
CPYEML |
||
|
Telephone |
CPYTEL |
||
|
Fax |
CPYFAX |
||
|
Mobile phone |
CPYMOB |
||
|
CRMCLOB |
CRM text file |
Contact (rel.) code |
CRCAINNUM |
|
BP code |
CRCBPRNUM |
||
|
Sales rep |
CRCREP |
||
|
CUNSESSION |
Stock count session |
From BP |
BPRNUMSTR |
|
To BP |
BPRNUMEND |
||
|
DADFCY |
DAS2 site |
Telephone |
TEL |
|
Email address |
|
||
|
DATEVBPACC |
DATEV BP assignment |
BP code |
BPRNUM |
|
DCLCUSVATBE |
Annual customer listing |
BP |
BPR |
|
Company name |
BPRNAM |
||
|
Telephone |
TEL |
||
|
DCLCUSVATBED |
BP |
BPR |
|
|
Company name |
BPRNAM |
||
|
DCLEECVATBE |
EU VAT statement (header) |
BP |
BPR |
|
Company name |
BPRNAM |
||
|
DCLEECVATBED |
EU VAT statement (detail) |
BP |
BPR |
|
DCLVATPORB |
VAT base information |
BP |
BPRNUM |
|
DCLVATPORL |
VAT declaration lines |
BP code |
BPRNUM |
|
DCLVATSPA |
Tax working table (SPA) |
BP code |
BPRNUM |
|
Company name |
BPRNAM |
||
|
DEB |
EU exchange declaration |
BP |
BPRNUM |
|
DMWBPREXC |
Waste disposal exceptions |
Business partner |
BPR |
|
DMWSCHEME |
Waste disposal scheme |
Business partner |
BPR |
|
DMWWEIGHT |
Waste disposal weight |
BP |
BPR |
|
DOOBPCINT |
Internal customers |
Customer code |
BPCNUM |
|
Customer |
BPCNAM |
||
|
DOOBPCLNK |
Order-giver association |
Service caller |
DOONUM |
|
Order-placer name |
DOONAM |
||
|
Customer |
BPCNUM |
||
|
Customer name |
BPCNAM |
||
|
DUDLNK |
Open item links |
BP |
BPR |
|
EDIBPRCPY |
EDI flows by BP/company |
BP |
BPRNUM |
|
EDIBPRCPYD |
BP |
BPRNUM |
|
|
EDIBPRPAR |
EDI partners by BP |
BP |
BPANUM |
|
EDITRKDOC |
Documents |
BP |
BPRNUM |
|
EFASISS |
Evt - asset disposal |
Buyer |
BUY |
|
ELEAACTU |
Evt - contract actualization |
Lessor |
LES |
|
ELEACRT |
Evt - contract creation |
Lessor |
LES |
|
ELEAEND |
Evt - end of contract |
Lessor |
LES |
|
ELEAPAY |
Evt - contract fee |
Lessor |
LES |
|
ELEARPU |
Evt - purchase option exercise |
Lessor |
LES |
|
ELEATRM |
Evt - contract termination |
Lessor |
LES |
|
ENVELOPPE |
Envelope |
BP |
BPRFIN |
|
EVCRESULT |
EU VAT ID check result |
BP number |
BPR |
|
BP name |
BPRNAM |
||
|
FACILITY |
Sites |
Name |
FCYNAM |
|
Bank account number |
BIDNUM |
||
|
Contact |
CNTNAM |
||
|
FAMPB |
Skill group |
Customer |
PBLBPC |
|
FAMPBREP |
Qualified employees |
Sales rep name |
REPNAM |
|
FUP |
Reminders conducted |
BP |
BPRFUP |
|
GACCDUDATE |
Open items |
Bill-to/Order BP |
BPR |
|
Pay-by |
BPRPAY |
||
|
GCOMMIT |
Commitments |
BP |
BPR |
|
GSTDTL |
GST detail |
BP |
BPR |
|
HISTODUD |
Open item archive |
Bill-to/Order BP |
BPR |
|
Pay-by |
BPRPAY |
||
|
HISTOOMM |
Mailing history |
BP code |
BPRNUM |
|
Contact (rel.) code |
CCNNUM |
||
|
HONPRV |
Service suppliers |
Telephone |
TEL |
|
Fax |
FAX |
||
|
INTERVEN |
Service response |
Customer |
BPC |
|
Contact (relationship) |
CCN |
||
|
Subcontractor |
SCONUM |
||
|
Telephone |
TEL |
||
|
Mobile phone |
MOB |
||
|
Email address |
EML |
||
|
ITMBPC |
Customer product |
Customer |
BPCNUM |
|
ITMBPS |
Supplier product |
Supplier |
BPSNUM |
|
ITMMASTER |
Products |
BP |
CFGBPRNUM |
|
LASTCUSMVT |
Last customer movements |
BP of movement |
BPCNUM |
|
LASTSUPMVT |
Last supplier movements |
BP of movement |
BPSNUM |
|
LEAD |
Leads |
Code |
PSTNUM |
|
Supervisor |
PSTREP |
||
|
Company name |
CPYNAM |
||
|
LEASE |
Lease contracts |
Lessor |
LES |
|
MACHINES |
Installed base |
End user |
MACCUTBPC |
|
BP code |
BPCNUM |
||
|
Contact (rel.) code |
CCNNUM |
||
|
Reseller |
MACRSL |
||
|
MACITN |
Machine installations |
End user |
BPC |
|
Reseller |
RSL |
||
|
MANDATE |
Mandates |
Customer code |
BPCNUM |
|
Bank account number |
BIDNUM |
||
|
MARASSREP |
Representative portfolio |
Sales rep |
REPNUM |
|
MARREPSEC |
Allocation of sectors |
Sales rep |
SCTREPSEC |
|
MARSCT |
Market sectors |
Sales rep |
MARSCTREP |
|
|
|
BP |
BPR |
|
MFGITM |
Work orders - products |
Destination |
BPCNUM |
|
MFGOPE |
Work order - operations |
BP |
BPRNUM |
|
MFGOPETRK |
Manufacture tracking - operati |
Supplier |
BPSNUM |
|
NOTE |
Notes |
Customer |
BPCNUM |
|
Supplier |
BPSNUM |
||
|
OPERATIONS |
Load in progress |
Supplier |
BPSNUM |
|
OPPOR |
Project |
Sales rep |
OPPREP |
|
BP |
OPPCMP |
||
|
Contact (relationship) |
OPPMCN |
||
|
ORDCOMP |
Service caller |
BP code |
BPRNUM |
|
ORDCOV |
WIP consideration history |
BP |
BPRNUM |
|
ORDERS |
WIP |
BP |
BPRNUM |
|
PAYVAT |
Cash VAT (Portugal) |
BP |
BPRNUM |
|
PBDGEND |
Payment balance decl details |
BP |
BPR |
|
PDPDET |
MPS calculation detail |
Source BP |
BPRNUM |
|
PHONECALL |
Call |
BP |
CLLCMP |
|
Contact (relationship) |
CLLCCN |
||
|
Outlook contact |
CLLCOR |
||
|
Direct line |
CLLETS |
||
|
Mobile phone |
CLLMOB |
||
|
Sales rep |
CLLREP |
||
|
|
CLLEML |
||
|
PHYELT |
Physical assets |
Supplier |
BPS |
|
PINVOICE |
Purchase invoices |
BP |
BPR |
|
Pay-by |
BPRPAY |
||
|
Company name |
BPRNAM |
||
|
Company name |
BPYNAM |
||
|
Freight agent |
FFWNUM |
||
|
SCD BP code |
SPACUSBPR |
||
|
Bank account number |
BVRBID |
||
|
PINVOICED |
Purchase invoice detail |
BP |
BPR |
|
Supplier |
BPSNUM |
||
|
PINVOICEV |
Costing purchase invoices |
BP |
BPR |
|
Bill-to customer |
BPCINV |
||
|
PITCOUNT |
Point counter |
Customer |
BPC |
|
PITDEB |
Points debit |
Customer |
BPR |
|
PITDEBD |
Point debits (line) |
Customer |
BPR |
|
PIWRK |
Temporary journal traceability |
BP |
BPRNUM |
|
Sales rep 1 |
REP1 |
||
|
Sales rep 2 |
REP2 |
||
|
PJMSOLITMD |
Sold product list |
Customer |
CUSTOMER |
|
PJMSOLITMH |
Sold product management |
Sold-to |
BPCORD |
|
Bill-to customer |
BPCINV |
||
|
Pay-by |
BPCPYR |
||
|
PJMTSKOPE |
Tasks - Operations |
BP |
BPRNUM |
|
PLMPAR |
PLM setup |
Email address |
ADDEML1 |
|
Email address |
ADDEML2 |
||
|
PORDER |
POs |
Supplier |
BPSNUM |
|
Company name |
BPRNAM |
||
|
Company name |
BPONAM |
||
|
Carrier |
BPTNUM |
||
|
Pay-to |
BPRPAY |
||
|
Invoicing BP |
BPSINV |
||
|
Freight agent |
FFWNUM |
||
|
Sold-to |
BPCORD |
||
|
PORDERC |
Cumulative POs before returns |
Supplier |
BPSNUM |
|
Freight agent |
FFWNUM2 |
||
|
PORDERQ |
POs quantities |
Supplier |
BPSNUM |
|
Invoicing BP |
BPSINV |
||
|
PORDITM |
Purchase orders by product |
Supplier |
BPSNUM |
|
PPRICLINK |
Purchase price list search (link) |
Supplier |
BPSNUM |
|
Carrier |
BPTNUM |
||
|
PPRIVARWRK |
Purchase price variance report |
Supplier |
BPSNUM |
|
Company name |
BPSNAM |
||
|
PQUOTATF |
RFQ supplier detail |
Supplier |
BPSNUM |
|
Company name |
BPRNAM |
||
|
PRECEIPT |
Receipt |
Supplier |
BPSNUM |
|
Company name |
BPONAM |
||
|
Billed-by supplier |
BPSINV |
||
|
Pay-to |
BPRPAY |
||
|
Carrier |
BPTNUM |
||
|
Freight agent |
FFWNUM |
||
|
PRECEIPTD |
Detail receipts |
Supplier |
BPSNUM |
|
Billed-by supplier |
BPSINV |
||
|
PREQUISD |
Purchase request detail |
Supplier |
BPSNUM |
|
PRESP |
RFQ responses |
Supplier |
BPSNUM |
|
PRESPD |
Detail RFQ responses |
Supplier |
BPSNUM |
|
PRETURN |
Returns |
Supplier |
BPSNUM |
|
Company name |
BPRNAM |
||
|
Invoicing BP |
BPSINV |
||
|
Pay-to |
BPRPAY |
||
|
Carrier |
BPTNUM |
||
|
Freight agent |
FFWNUM |
||
|
PRETURND |
Detail return |
Supplier |
BPSNUM |
|
Invoicing BP |
BPSINV |
||
|
PROJET |
Project |
BP |
BPRFIN |
|
PWRKPND |
Return line detail temporary |
Supplier |
BPSNUM |
|
Invoicing BP |
BPSINV |
||
|
PWRKPNH |
Temporary return |
Supplier |
BPSNUM |
|
Company name |
BPRNAM |
||
|
Billed-by supplier |
BPSINV |
||
|
Pay-to |
BPRPAY |
||
|
Carrier |
BPTNUM |
||
|
Freight agent |
FFWNUM |
||
|
PWRKPOC |
Temporary product-contract |
Freight agent |
FFWNUM2 |
|
PWRKPQF |
RFQ ADR supplier temporary |
Supplier |
BPSNUM |
|
Company name |
BPRNAM |
||
|
PWRKPTH |
Temporary receipt |
Supplier |
BPSNUM |
|
Billed-by supplier |
BPSINV |
||
|
Pay-to |
BPRPAY |
||
|
Carrier |
BPTNUM |
||
|
Freight agent |
FFWNUM |
||
|
RBKBELDET |
Belgian bank statement detail |
BP code |
BPRNUM |
|
Company name |
BPRNAM |
||
|
Bank account |
ACCBAN |
||
|
Temporary account |
ACCTMP |
||
|
RBKBELHEA |
Belgian bank statement |
Recipient name |
DESTNAM |
|
Bank account number |
BIDNUMBAN |
||
|
Account holder name |
ACCNAM |
||
|
Account description |
ACCDES |
||
|
RELMT940D |
File FMT940 (lines) |
Bank account number |
BIDNUM |
|
BP |
BPRPAY |
||
|
Bill-to BP |
BPRINV |
||
|
REPSEC |
Secondary marketing contacts |
Customer code |
BPCNUM |
|
Sales rep code |
REPNUM |
||
|
RESRES |
Resource reservations |
Reserved by |
RERREP |
|
RITENZIONE |
Table of retention codes |
Cash account |
ACC1 |
|
Charge account |
ACC2 |
||
|
RITMVT |
Retention movements |
BP |
BPR |
|
RNWPREP |
Renewal |
Grantor |
CCNUSR |
|
ROUOPE |
Routing - operations |
BP |
BPRNUM |
|
ROUOPESTD |
Standard operations |
BP |
BPRNUM |
|
RSLINESGER2 |
Recapitulative statement |
Offset |
OFFACC |
|
SALESREP |
Sales rep |
Sales rep |
REPNUM |
|
Last name |
REPNAM |
||
|
SBGEO |
Consulting fields of service suppliers |
Service supplier code |
BPRNUM |
|
SBODLINK |
Component qty. calculation (link) |
Sold-to |
BPCORD |
|
Bill-to customer |
BPCINV |
||
|
Group customer |
BPCGRU |
||
|
Pay-by |
BPCPYR |
||
|
Carrier |
BPTNUM |
||
|
SBPBL |
Service suppliers' skills |
Service supplier code |
BPRNUM |
|
SCHGH |
Stock change header |
Subcontractor |
BPSNUM |
|
Customer |
BPCNUM |
||
|
SCOHEAD |
Subcontract order |
Supplier |
BPRNUM |
|
SCOITM |
Supplier |
BPRNUM |
|
|
SCOSRV |
Order sub-contract services |
Supplier |
BPRNUM |
|
SCOTRK |
Sub-contract tracking |
Supplier |
BPRNUM |
|
SDELIVERY |
Delivery header |
Sold-to |
BPCORD |
|
Bill-to customer |
BPCINV |
||
|
Pay-by |
BPCPYR |
||
|
Group customer |
BPCGRU |
||
|
Ship-to customer name |
BPDNAM |
||
|
Delivery contact |
CNDNAM |
||
|
Bill-to customer name |
BPINAM |
||
|
Invoice contact |
CNINAM |
||
|
Sales rep |
REP |
||
|
Carrier |
BPTNUM |
||
|
Freight agent |
FFWNUM |
||
|
SDELIVERYD |
Delivery detail |
Sold-to |
BPCORD |
|
Sales rep 1 |
REP1 |
||
|
Sales rep 2 |
REP2 |
||
|
SEARESULT |
Search result |
Record code |
OBJNUM |
|
SEAUTH |
Credit card authorizations |
Customer |
BPCNUM |
|
SEBPC |
Payment gateway customer data |
Customer |
BPCNUM |
|
Name |
ACCNAM |
||
|
Email address |
|
||
|
SECPST |
Lead sector |
Sales rep |
SPTREP |
|
SELCMGLIS |
Marketing selection guide |
BP code |
BPRNUM |
|
Sales rep code |
REPNUM |
||
|
SERREQUEST |
Service requests |
Service caller |
SREDOO |
|
Customer |
SREBPC |
||
|
Contact (relationship) |
SRECCN |
||
|
Bill-to customer |
SREBPCINV |
||
|
Pay-by |
SREBPCPYR |
||
|
Group customer |
SREBPCGRU |
||
|
Sales rep |
SREREP |
||
|
SETXN |
Credit card transactions |
Name |
ACCNAM |
|
Email address |
|
||
|
Customer |
BPCNUM |
||
|
SHIPDOC |
Shipment documents |
BPs |
SDBP |
|
SHIPMENT |
Shipment |
BP code |
BPRNUM |
|
Supplier |
BPSNUM |
||
|
Carrier |
BPTNUM |
||
|
SINVOICE |
Sales invoices |
BP |
BPR |
|
Pay-by |
BPRPAY |
||
|
Company name |
BPYNAM |
||
|
Company name |
BPRNAM |
||
|
SINVOICED |
Sales invoice detail |
Bill-to customer |
BPCINV |
|
Sales rep 1 |
REP1 |
||
|
Sales rep 2 |
REP2 |
||
|
SINVOICEV |
Costing sales invoice |
Bill-to customer |
BPCINV |
|
Sold-to |
BPCORD |
||
|
Group customer |
BPCGRU |
||
|
Bill-to customer name |
BPINAM |
||
|
Invoice contact |
CNINAM |
||
|
Ship-to customer name |
BPDNAM |
||
|
Delivery contact |
CNDNAM |
||
|
Pay-by |
BPRPAY |
||
|
Sales rep |
REP |
||
|
Freight agent |
FFWNUM |
||
|
SOI |
Statement creation |
BP |
BPR |
|
SORDER |
Sales orders - header |
Sold-to |
BPCORD |
|
Bill-to customer |
BPCINV |
||
|
Pay-by |
BPCPYR |
||
|
Group customer |
BPCGRU |
||
|
Sold-to customer name |
BPCNAM |
||
|
Person to contact |
CNTNAM |
||
|
Bill-to customer name |
BPINAM |
||
|
Invoice contact |
CNINAM |
||
|
Ship-to customer name |
BPDNAM |
||
|
Delivery contact |
CNDNAM |
||
|
Sales rep |
REP |
||
|
Carrier |
BPTNUM |
||
|
Freight agent |
FFWNUM |
||
|
SORDERC |
Sales orders - early/late |
Sold-to |
BPCORD |
|
Freight agent |
FFWNUM |
||
|
SORDERP |
Sales orders - price |
Sold-to |
BPCORD |
|
Delivery contact |
CNDNAM |
||
|
Bill-to customer |
BPCINV |
||
|
Sales rep 1 |
REP1 |
||
|
Sales rep 2 |
REP2 |
||
|
SORDERQ |
Sales orders - quantities |
Sold-to |
BPCORD |
|
Carrier |
BPTNUM |
||
|
SPACK |
Delivery package |
Sold-to |
BPCORD |
|
SPPRTCONF |
Price catalog definition |
From customer |
BPCSTR |
|
To customer |
BPCEND |
||
|
SPRICLINK |
Sales price list search |
Bill-to customer |
BPCINV |
|
Group customer |
BPCGRU |
||
|
Carrier |
BPTNUM |
||
|
SPRICPRTQ |
Sales price catalog |
Sold-to |
BPCORD |
|
SQUOTE |
Quote header |
Customer |
BPCORD |
|
Customer name |
BPCNAM |
||
|
Order contact |
CNCNAM |
||
|
Ship-to customer name |
BPDNAM |
||
|
Delivery contact |
CNDNAM |
||
|
Sales rep |
REP |
||
|
Freight agent |
FFWNUM |
||
|
SQUOTED |
Quote detail |
Sold-to |
BPCORD |
|
Sales rep 1 |
REP1 |
||
|
Sales rep 2 |
REP2 |
||
|
Delivery contact |
CNDNAM |
||
|
SRETURN |
Sales return header |
Sold-to |
BPCORD |
|
Ship-to customer name |
BPDNAM |
||
|
Delivery contact |
CNDNAM |
||
|
Bill-to customer |
BPCINV |
||
|
Freight agent |
FFWNUM |
||
|
STOALL |
Allocations |
BP |
BPRNUM |
|
STOJOU |
Stock journal |
BP |
BPRNUM |
|
STOLOT |
Lot numbers |
Supplier |
BPSNUM |
|
STOPREH |
Pick ticket header |
Sold-to |
BPCORD |
|
Carrier |
BPTNUM |
||
|
STOPRELIS |
Shipment preparation list |
Sold-to |
BPCORD |
|
Carrier |
BPTNUM |
||
|
STOPRELISW |
Work preparation lists |
Sold-to |
BPCORD |
|
Carrier |
BPTNUM |
||
|
STOPREW |
Work preparation sheet |
Sold-to |
BPCORD |
|
Bill-to customer |
BPCINV |
||
|
Carrier |
BPTNUM |
||
|
STOQUAL |
Quality control |
BP |
BPRNUM |
|
STOREO |
Reorder |
BP |
BPRNUM |
|
STOSER |
Serial numbers |
Customer |
BPCNUM |
|
STOSRG |
Storage |
BP |
BPRNUM |
|
STOSYNW |
Stock resynch work |
BP |
BPRNUM |
|
STOTRK |
Traceability |
BP |
BPRNUM |
|
SUBCONT |
Service supplier |
BP code |
BPRNUM |
|
SVCRINVCND |
Scheduled invoice |
Sold-to |
BPCORD |
|
Bill-to customer |
BPCINV |
||
|
SWIIMPBVR |
Import Swiss ISR file |
Business partner |
BPR |
|
SWIIMPTMP |
Import Swiss ISR file (temp.) |
Business partner |
BPR |
|
SWRKDLV |
Automatic delivery generation |
Sold-to |
BPCORD |
|
Bill-to customer |
BPCINV |
||
|
TABACCINT |
Intercompany account mapping |
Source debit |
ACCSRCDEB |
|
Source credit |
ACCSRCCDT |
||
|
Target debit |
ACCTGRDEB |
||
|
Target credit |
ACCTGRCDT |
||
|
Source BP |
BPRSRC |
||
|
Target BP |
BPRTGR |
||
|
TABPLACE |
Transit area |
Supplier |
BPSNUM |
|
TABPLACETIME |
Transport lead time |
Carrier |
BPTNUM |
|
TABVATEXE |
Tax exemption table |
Customer |
BPCNUM |
|
TASK |
Task |
BP |
TSKCMP |
|
Contact (relationship) |
TSKCCN |
||
|
Outlook contact |
TSKCOR |
||
|
Sales rep |
TSKREP |
||
|
TAUTILIS |
SAFE X3 WAS users |
BP |
BPRNUM |
|
|
|
||
|
TAXLINK |
Tax calc. basis calculation (link) |
BP |
BPRNUM |
|
TDSPRV |
Fee total/service supplier |
BP |
BPRNUM |
|
TMP2855 |
Temporary table Fisc. Stmt 2855 |
Company name |
CPYNAM |
|
TMPCNSBAN |
Bank inquiry |
BP |
BPR |
|
Bank account number |
BID |
||
|
TMPCNVECAR |
Exch. rate temporary table |
BP |
BPR |
|
TMPCSRQ |
Temporary cash requirements |
Bill-to BP |
BPR |
|
Name |
BPRNAM |
||
|
TMPEXPENSE |
Temporary table - Expenses |
Miscellaneous BP |
EXPBPR |
|
TMPFUP0 |
Campaign criteria |
From customer |
BPCDEB |
|
To customer |
BPCFIN |
||
|
Group customer |
BPCGRU |
||
|
Risk BP |
BPCRSKSTR |
||
|
Risk BP |
BPCRSKEND |
||
|
From sales rep |
REPDEB1 |
||
|
To sales rep |
REPFIN1 |
||
|
From sales rep |
REPDEB2 |
||
|
To sales rep |
REPFIN2 |
||
|
From sales rep |
REPDEB |
||
|
To sales rep |
REPFIN |
||
|
TMPFUP1 |
BPs for reminding |
Bill-to/Order BP |
BPC |
|
TMPFUP2 |
Open items to remind |
BP |
BPC |
|
TMPLEARNT |
Temporary table |
Company name |
CPYNAM |
|
TMPLOFGRP |
Temporary table |
Company name |
CPYNAM |
|
Name |
FCYNAM |
||
|
Supplier |
BPR |
||
|
TMPMASLEA |
Contract actions temp table |
Lessor |
LES |
|
TMPPAYDUD |
Temporary payment proposal |
BP |
BPR |
|
Bank account number |
BID |
||
|
TMPPAYDUD2 |
BP |
BPR |
|
|
Company name |
BPRNAM |
||
|
TRANNOTEH |
Transportation note |
BP |
BPRNUM |
|
Ship-to customer name |
BPDNAM |
||
|
Delivery contact |
CNDNAM |
||
|
Ship-from |
SHIFRMNAM |
||
|
TRANSPORT |
Transport |
Carrier |
BPTNUM |
|
BP code |
BPRNUM |
||
|
UNFILWRK |
Unfilled orders report |
Sold-to |
BPCORD |
|
UPORDER |
PO history |
Supplier |
BPSNUM |
|
Company name |
BPRNAM |
||
|
Company name |
BPONAM |
||
|
Carrier |
BPTNUM |
||
|
Pay-to |
BPRPAY |
||
|
Supplier invoice |
BPSINV |
||
|
Freight agent |
FFWNUM |
||
|
Sold-to |
BPCORD |
||
|
UPORDERQ |
PO quantity history |
Supplier |
BPSNUM |
|
Invoicing BP |
BPSINV |
||
|
VATLINITMGER |
German VAT line items |
BP |
BPR |
|
VSORDER |
Sales order history - header |
Sold-to |
BPCORD |
|
Bill-to customer |
BPCINV |
||
|
Pay-by customer |
BPCPYR |
||
|
Group customer |
BPCGRU |
||
|
Sold-to customer name |
BPCNAM |
||
|
Person to contact |
CNTNAM |
||
|
Bill-to customer name |
BPINAM |
||
|
Invoice contact |
CNINAM |
||
|
Ship-to customer name |
BPDNAM |
||
|
Delivery contact |
CNDNAM |
||
|
Sales rep |
REP |
||
|
Carrier |
BPTNUM |
||
|
Freight agent |
FFWNUM |
||
|
VSORDERC |
Cumulative sales order history |
Sold-to |
BPCORD |
|
Freight agent |
FFWNUM |
||
|
VSORDERP |
Sales order history - price |
Sold-to |
BPCORD |
|
Delivery contact |
CNDNAM |
||
|
Bill-to customer |
BPCINV |
||
|
Sales rep 1 |
REP1 |
||
|
Sales rep 2 |
REP2 |
||
|
VSORDERQ |
Sales order history - Qties. |
Sold-to |
BPCORD |
|
Carrier |
BPTNUM |
||
|
WAREHOUSE |
Warehouses |
Name |
WRHNAM |
|
WARFLYER |
Warranty vouchers |
Site name |
BPANAM |
|
WARREQCPN |
Warranty request lines |
Reseller |
RSL |
|
WARREQUEST |
Warranty requests |
Customer |
BPC |
|
Contact (relationship) |
CCN |
||
|
WHTDTL |
WHT detail |
BP |
BPR |
|
WSTOALL |
Allocations |
BP |
BPRNUM |
|
WSTOREO |
Reorder |
BP |
BPRNUM |
|
Table |
Description |
Description |
Field |
|
AIN |
Contact (relationship) |
|
|
|
AUS |
User |
|
|
|
BID |
Bank account number |
|
|
|
BPA |
Address |
|
|
|
BPC |
Customer |
|
|
|
BPR |
Business partner |
|
|
|
BPS |
Supplier |
|
|
|
BPT |
Carrier |
|
|
|
COR |
Outlook contact |
|
|
|
E164TEL, TEL, TELTC |
Phone numbers/fax numbers |
|
|
|
FNA |
First name |
|
|
|
GAC |
Account (general or individual) |
|
|
|
LDS |
Lead |
|
|
|
MAI |
Email address |
|
|
|
NAM |
Names |
|
|
|
REP |
Sales representative |
|
|
Specifically for the Sage X3 HR & Payroll modules, the standard data types associated with main personal data records are as follows:
|
Data type |
Description |
|
EML |
Employee ID |
And fields, contents, and location:
|
Table |
Description |
Field |
Description |
Data Type |
|
EMPLOID |
Civil status |
REFNUM |
Employee ID |
EML |
|
SRN |
First name |
A |
||
|
NAM |
Name |
A |
||
|
CIV |
Title |
C |
||
|
PSD |
Known as |
NAM |
||
|
DATBRN |
Date of birth |
D |
||
|
EMPPIC |
Photo |
ABB Image file |
||
|
SEX |
Gender |
M |
||
|
NTT |
Nationality Code |
CRY |
||
|
CRYNAM |
Country name |
NCY |
||
|
CTYBRN |
Municipality |
A |
||
|
ADD1/ADD2/ADD3 |
Address |
ADL |
||
|
CTY |
City |
CTY |
||
|
CODPOS |
Postal Code |
POS |
||
|
TEL |
Telephone |
TEL |
||
|
MOB |
Mobile phone |
TEL |
||
|
FAX |
Fax |
TEL |
||
|
EML |
|
A |
||
|
NAMCNT |
Person of contact: Name |
NAM |
||
|
SRNCNT |
Person of contact: First name |
NAM |
||
|
TELCNT |
Person of contact: Telephone |
TEL |
||
|
MOBCNT |
Person of contact: Mobile phone |
TEL |
||
|
EMLCNT |
Person of contact: Email |
A |
||
|
EMPLOCHD |
Children |
CHDNAM |
Name |
A |
|
CHDSRN |
First Name |
A |
||
|
CHDSEX |
Gender |
M |
||
|
DATCHDBRN |
Date of Birth |
D |
||
|
EMPLOJNT |
Spouses (>1) |
SSITFAM |
Marital Status |
C |
|
SJNTREFNUM |
Spouse's registration number |
MAT |
||
|
SJNTNAM |
Spouse's name |
A |
||
|
SJNTSRN |
First name |
A |
||
|
SJNTDATBRN |
Date of birth |
D |
||
|
SJNTTEL |
Telephone |
TEL |
||
|
EMPLOAD |
Administrative information |
FLGHDC |
Disabled worker |
M |
|
HDC |
Handicap rate |
DCB |
||
|
EMPLORIB |
Bank details |
BIDNUM |
Bank account number |
BID |
|
EMPLOMED |
Medical examinations |
MEDDCT |
Doctor |
A |
Security principles
To minimize the risk of data breaches and related penalties, some elementary security principles are recommended. This chapter highlights these principles but it does not prevent you from reading the entire document.
These principles relate to versions V11.0.8, GX V11.0.6, V12.0.14, HR V12.0.8, GX V12.0.19 and 2018 R3. If you use another version, refer to the documentation available for the version you run for more details.
Main principles
Although it remains the customer's responsibility to ensure the system and network are secure, the solution platform provides you with some principles to support this:
- Standard web browsers and HTTP or HTTPS protocols are used. The web technology provides a first level insulation between the web server and the workstation.
- Passwords are not transferred on the network. The authentication system is based on standards. It can be a Windows login that is controlled in an LDAP directory, or an Oauth2 authentication (a redirection is done to the authentication server). For the sake of simplicity (or for autonomous demo servers), a fallback solution based on users and encrypted passwords stored in the solution web server is available. However, it should not be used for production environments.
- The connection between the solution web server and the solution server is based on certificates that are created during the installation by a private certificate authority.
- Rights management is done at the service level and is based on function profiles associated with the user. It is possible to manage the permissions at an elementary level, function, and action up to the field. It is possible, for example, to obfuscate information depending on the role of the user.
- Access to the server by the solution processes is restricted by a white list of authorized directories.
- On the solution web server, node.js and MongoDB do not require all processes and/or services to be root or have administrator privileges.
As a consequence, password management is now different from versions before V7.1 because the security rules for passwords are now managed by the security provider (Google, LDAP) you choose.
Security parameters
The Syracuse web server has different parameters to fine tune the security. The configuration is based on a dedicated security section in the nodelocal.js file.
HTTP headers
Clickjacking
The server is protected against clickjacking by adding the x-frame-options: DENY HTTP header.
If for any reason you need to put the site in an iFrame, you can do it at your own risk by overriding the default as follows:
exports.config = {
security: {
http: {
headers: {
// set 'x-frame-options' to enable embedding into another site via iframe
// 'x-frame-options': 'allow-from http://other-site',
'x-frame-options': 'SAMEORIGIN', // default value is 'DENY'
},
},
},
};
Before U9.0.3, the header was directly under the HTTP as follows:
exports.config = {
security: {
http: {
// set 'x-frame-options' to enable embedding into another site via iframe
// 'x-frame-options': 'allow-from http://other-site',
// 'x-frame-options': 'SAMEORIGIN',
'x-frame-options': 'DENY' // default value
},
},
};
XSS and other defense headers
Any header in the headers property is added to the response. By default, the following are added:
x-content-type-options: nosniff: Prevents Internet Explorer and Google Chrome from MIME-sniffing.x-xss-protection: 1; mode=block: Enables the Cross-site scripting (XSS) filter built into most recent web browsers.content-security-policy: frame-ancestors 'self': New standard to prevent clickjacking and that allows your site only.
The content-security-policy has many directives you can use to control what the browser can render. Among all directives, we can mention:
script-src: Trusts only script sources in the list.child-src: Trusts only embedded content in the list. This directive controls what can be loaded in an iFrame.frame-ancestors: Similar to the x-frame-options header, but if both exists, the W3C specifications mention that frame-ancestors must be used.
These directives can be modified as sub-properties of content-security-policy as follows:
exports.config = {
security: {
http: {
headers: {
"content-security-policy": {
"child-src": ["'self'", "www.w3schools.com"
]
},
},
},
};
HTML5 rocks provides a good tutorial on the subject.
Content security
The user interface can include external content by using an iFrame. Including such content may put the security of the site at risk, but you can reduce that risk by adding the sandbox attribute to the iFrame HTML tag.
iFrame sandbox
HTML gadgets support 3 levels of security (low, medium, high) depending on what you want to authorize.
These levels define the sandbox attribute as follows:
- low: "allow-same-origin allow-forms allow-popups allow-scripts"
medium: "allow-forms allow-scripts"high: ""
Customizing the sandbox
You can change the default values of the three levels by editing the security section of the nodelocal.js file.
exports.config = {
security: {
client: {
iframe: {
sandbox: {
// allow- forms Enables form submission
// allow-pointer- lock Enables pointer APIs (for example pointer position)
// allow- popups Enables popups
// allow-same- origin Allows the iframe content to be treated as being from the same origin
// allow- scripts Enables scripts
// allow-top- navigation Allows the iframe content to navigate its top-level browsing context
// low: null, // if null no sandbox attribute is added
(not recommended)
// medium: null, // if null no sandbox attribute is added
(not recommended)
// medium: "",
medium: "allow-same-origin allow-forms allow-scripts",
// high: ""
}
}
},
},
};
By combining the sandbox attribute and the child-src directive of the content-security-policy, you can have a better control of what can be rendered in the browser.
Security best practices
Security has been a strong focus in the design and development of the solution, which has been audited and certified by an external authority for safe operation in the cloud.
A security policy is always compromised by its weakest link. It is therefore critical to pay attention to the security of your system, and to use all available tools for this.
This document summarizes what you should pay attention to when implementing the solution.
General security guidelines
Securing your solution on-premise architecture should not be considered optional. Sensitive or personal data, such as customer details, financial records, or staff information, is stored using your business software. This may be stored on your own servers, if you have in-house systems, or outside your business if you use cloud computing services.
You get maximum security for your data without any action if you use Sage X3 cloud. However, if you choose to install the solution as an on-premises instance, or if you host it with a non-Sage managed cloud provider, there are a few rules to follow. It is important to take a multi-layered, industry proven approach to keep your data where it belongs and as secure as possible. This document reviews the main controls you should implement to secure your data.
General guidelines
Always use HTTPS if your server is visible on the internet
The solution is a web application that can be accessed using an HTTP or HTTPS connection. Although HTTP is available, we recommend you always use https for production instances, especially if your solution is accessed from the public internet.
Use strong passwords
Make sure you change the default administrator password to a strong password after the application setup. Ideally, it should:
- Contain six characters minimum; the longer the password is, the stronger it is.
- Use a combination of digits, uppercase and lowercase letters, and symbols such as @ # $ % ! ? &, etc.
- Not contain words that can be found in dictionaries or that are part of the user name.
- Not contain a keyboard pattern such as "qwerty."
- Not contain your date of birth.
Always use advanced authentication on a production instance
The solution supports several state-of-the-art services (such as LDAP and OAuth2) that should be used for user authentication on production instances, or on any instance holding sensitive data. Refer to the guides on setting up advanced authentication for more details.
We do not recommend using basic authentication (user and password) except on implementation or test instances. Even then, make sure those instances do not contain any sensitive data because basic authentication exposes you to inside and outside threats.
Secure your servers with tight user access rights
The servers that host the solution components contain configuration files and other data vulnerable to inside threats. Administrators should be the only persons allowed to log in to the servers. Make sure you set up users for the solution administration with the appropriate rights to the relevant directories.
The solution servers should be built using industry-standard guidelines that are freely available.
Use local firewalls
Use local firewalls on your servers to lock any IP port that is not needed to operate the solution or for user access. Typically, if all the solution components are installed on a single server, the solution only needs the HTTP or HTTPS ports to function. For multiple-server installations, you need to open the ports (or ranges of ports) that the solution components use to communicate with each other.
Building a secure internet architecture
The architecture you implement is key to your security, especially if your system can be accessed from the public internet. To connect your systems and make them available from the internet, you have to decide:
- Which servers and ports need to be seen from the outside world.
- How any of the queries coming from the outside world are intercepted, translated, and directed to those servers and ports, if applicable.
This involves equipment such as:
- A firewall, which sits between your internal network and the internet to intercept incoming queries and forward them to the proper servers inside your network.
- A Demilitarized Zone or DMZ, which is a physical or logical network area that isolates your LAN from the internet.
The firewall is the guard at your DMZ’s checkpoints.
Recommended firewall settings if your instance is visible on the public internet
The solution uses several components that communicate together through IP ports. The only port that actually needs to be accessed by users for the solution to operate is the HTTP or HTTPS port (8124 or 843 by default). All other ports can (and must) be protected from external access, especially if the server is accessible from the internet. The MongoDB port (27017 by default) and the Elasticsearch port (9200 by default) are examples of ports that should not be available.
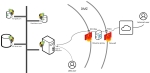
Ideally, your solution HTTPS port should not be reachable directly from the public internet, but rather through a DMZ and reverse proxy, as shown in the example below:
Alternatively, you can expose the web (Syracuse) server alone, with all ports protected except HTTPS, and with the strongest possible authentication service (not basic). All other servers should then be placed safely in your LAN.
Security implementation in details
Authentication
The solution supports several identity providers, such as:
- LDAP (for on-premise installations only)
- Oauth2 (with a Gmail account or a Microsoft account)
- Sage ID
This improves security by offloading the management of user credentials that do not transit through the ERP (when integrated with Oauth2 identity providers or with a Sage ID). It also improves the user experience by providing a Single Sign-On (SSO) experience.
Authorization
On the web platform
Once authenticated, users are connected to the platform with a user login account. Each user belongs to at least one group, and each group is associated with a role.
When logging in, the user can select the role to use among the list of authorized roles. This role is linked to a security profile which is associated with a level: 0 to 99, 0 being the most powerful.
The security profile defines the privileges a user has on platform operations. Make sure you assign a set of roles with appropriate security profiles to each user. As the platform administrator, you can define as many roles and security profiles as necessary.
A security profile can grant 12 different privileges, of which the following are critical for security:
- myProfile allows users to modify information related to their own identification (name, password, email address, photo). It also grants them read access to their own context (sessions they opened, endpoints they have access to, etc.). This access can be granted to most users.
- Users allows the definition of new users and should be granted only to platform administrators. However, modification rights can be granted to some key users. They are then able to modify the information associated to users with lower security profiles.
- TechnicalSettings allows access to the technical configuration (endpoints, $$PRODUCT solutions, etc.). It should only be granted to the persons in charge of the platform technical administration.
- Development allows access to resources for users working on extending the standard by bespoke or vertical developments.
On the folders
What we call a folder is the repository that contains business data related to one or more companies having one or more sites (each company is linked to a legislation code). A folder is identified as an endpoint on the platform. Groups specify the endpoints a user is allowed to connect to. This list is critical for security.
A user who connects to the platform is identified by a user code in each folder. By default, the user code and the user login account are the same. However, it is possible to redefine the user code for each endpoint in the user administration page.
In each folder, it is possible to define access to the information at a very detailed level:
- A user has a function profile, and can have read, write, delete, and execute access on every function. If the function manages data associated with companies or sites, the authorizations can be set up differently for each company and/or site.
- Row level permissions filter data on any property. For example, a user is only authorized to access the list of customers of a given sales order.
- Access codes restrict the access to records or properties so that only selected users can see and edit them.
- Access to reports can be filtered with access codes for each user and report. However, it is simpler to manage them by groups, and grant rights for each group.
Use these features to set up the access to critical data differently on each folder for a given user.
For each folder, there is a main administrator user code. It is ADMIN by default, but you can change in the the ADMUSR - Super user parameter (SUP chapter, SEC group). Only use this user code for tasks that require it.
Network security
As the solution runs on multiple physical or logical servers connected through a server, the security of this network is very important. The best practices for network security are as follows:
- Only open access to the servers on the ports that are necessary for normal use. For example, only open the HTTP (80 by default) and HTTPS (443 by default) ports on the server running node.js.
- Install and set up firewalls and all the tools needed to ensure physical security.
- Client connections can run in HTTP or HTTPS mode. Using HTTPS is strongly recommended if the connected device accesses the web server through the internet.
- To secure the connection between different environments, the solution uses certificates, which are generated during installation with a master certificate. The private key of this master certificate must be kept safe on a computer with restricted access.
Database security
Databases must be secured following the principles listed below.
Relational database
The server on which the relational database is installed must not be exposed over the network.
Only the solution server (application/runtime) and the report server can access RDBMS. Execution servers and report servers are proxies that get the data requested by external services. Never set up the database connection to the platform with the database administrator account. This account is only required for some configuration steps, and it can be changed later.
MongoDB database
The servers on which the document database is installed must not be exposed over the network. Only the web server (node.js) needs access to the MongoDB database.
Search engine
The servers on which Elasticsearch is installed must not be exposed over the network. It should only be accessible from the node.js servers. The solution platform sends the query to Elasticsearch with additional security filters, based on the privileges of the user. When you access the Elasticsearch server directly, you can bypass these security filters: this compromises security by returning all the relevant indexed data.
File system security
The file system security of the different servers should be implemented with the relevant tools (antivirus, network access security, etc.) at the right level. Make sure these tools do not cause performance issues. For example, avoid running a continuous antivirus scan on a database server.
On application and process servers, the solution engine runs in a sandbox. This allows you to control the system commands that are launched, and the location where files can be read, created, modified, or deleted. This prevents malicious code written for the execution engine from running operating system commands (by using system instructions).
Setting up the sandbox is recommended, especially if you operate in a cloud, or if the solution code is supplied by external vendors.
Development rules
The solution is supplied with a developer workbench that allows bespoke development. This can bring additional security threats that you can address with the following best practices:
SQL injection
The solution language includes ExecSQL and SQL functions with an argument that can be evaluated. All data used to build SQL statements must be properly escaped.
HTML injection
This security issue can only happen when additional graphical components are added to the user interface. At the moment, the extensibility tool is only available for early adopters. Detailed security guidelines are given to developers, but they are out of the scope of this document. A dedicated security audit is done on additional components supplied by external providers to prevent this risk.
Audit
The solution includes a set of tools that might be activated in production. This is a best practice after a period of operation, especially with the following tools:
- An audit trail of all the operations. The parameter that activates this audit trail is called TABTRA. According to its value, you can set up a recording on all the operations, or only on the deletion /renaming operations. It can be set up at the user level, or more globally.
- An audit collection (from V12) can be set up on administrative data in MongoDB.
- Database triggers. They can be set on tables to store previous and new values of given columns, based on simple conditions.
- A workflow engine. It can store any information related to triggering events that can be set up with various conditions in a history table.
Data retention rules
All local laws enforce some minimum data retention rules about data, transactions and reports.
You can find here, for informational purposes only, some examples of retention rules that apply for countries where the solution operates.