Features that can help you with personal data protection
Ease of access to the right information and process
If someone is responsible for personal data protection in your business, they are most likely not experts in the use of the solution nor its numerous tools for manipulating and storing personal data.
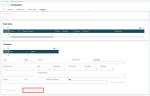
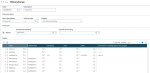
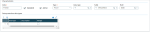
As such, you can design and allocate dedicated home pages for such people. You can group the information they need on a dashboard and design visual processes for them to easily access the relevant functions.
From V11.0.8, GX V11.0.6, V12.0.14, HR V12.0.8, GX V12.0.19 and 2018 R3, a new standard visual process dedicated to personal data protection is delivered, with all relevant links to the appropriate features. It is intended to provide a base you can easily adapt to your own processes and organization, as required. The following screenshot shows you the process delivered:
Data Protection Officer (DPO) management
The process to identify a DPO, or if you want to record the individuals responsible for data protection, is described below.
You can use the following features:
Assign the DPO role to one of the contacts defined in the company master record. A new checkbox has been added for this purpose. This feature is delivered as a standard presetting from V11.0.8, GX V11.0.6, V12.0.14, HR V12.0.8, GX V12.0.19 and 2018 R3.
- In the previous versions, you can use any other information to identify the DPO such as the role code that can be freely defined.
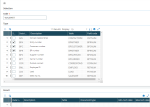
- From V11.0.8, GX V11.0.6, V12.0.14, HR V12.0.8, GX V12.0.19 and 2018 R3, a log provides you with all the companies in your group and their corresponding data protection officers. This log includes both the companies in and outside the EU to identify potential legal constraints you must solve by establishing contracts.
For the Sage X3 HR & Payroll solution, this would be by site.
Attachments
If you want to keep track of administrative events linked to data protection, such as consents, data access rights and alteration, you can attach documents to any record. From the master record, an attachment link opens a page where you can create links associated with keywords that can be freely defined such as consents linked to customers.
Auditing tools
To manage the security linked to personal data, it is advised to put in place security and audit parameters regardless of the technology used.
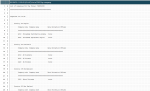
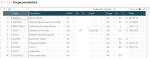
One of the tools provided by the solution is the setup of an audit that can be triggered when accessing any function and performing any modifications. This can be done for creations, updates, and deletions. It stores the values (before and after modification) in the audit trail fields. The audit can also be focused and conditioned. In the example below, the creation, modification, and deletion of customers are tracked as soon as the first contact date is after a given date:
This feature automatically creates database triggers that ensure the traceability of modifications, regardless of the way the updates were performed.
With the solution, you can set the audit of any record, track all changes, or just a deletion or value change. This parameter can be set up at the user level and is managed by a Supervisor function.
Query tool
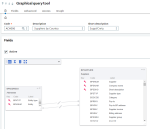
If you want to extract data for search and auditing purposes, the solution integrates various reporting tools including an on-demand query tool.
The result of such a request can generate PDF files, Excel spreadsheets, CSV files, and many other formats. When run, the query tool performs a strict filtering of the data based on the rights given to the user. The recommendation is to use requests that are not shared if they are authorized for several users, unless all these users have the same rights.
Data types related to personal data
Being metadata-based, the solution can assist you in identifying personally identifiable information. Every piece of data is attached to a data type as shown in the Documentation section.
This list can be used to analyze the data dictionary and identify where personal data is used and stored.
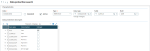
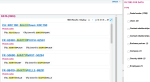
From V11.0.8, GX V11.0.6, V12.0.14, HR V12.0.8, GX V12.0.19 and 2018 R3, this analysis has been automated. A new tool delivered within the solution produces a CSV file listing all the fields linked to a data type. The result of this extraction looks as follows:
"Table";"Description";"Field";"Description" … "BPADDRESS";"Addresses";"BPANUM";"Entity" "BPADDRESS";"Addresses";"TEL";"Telephone" "BPADDRESS";"Addresses";"FAX";"Fax" "BPADDRESS";"Addresses";"MOB";"Mobile phone" "BPADDRESS";"Addresses";"WEB";"Internet address" "BPARTNER";"Business partner";"BPRNUM";"BP" "BPARTNER";"Business partner";"BPRNAM";"Company name" "BPARTNER";"Business partner";"CNTNAM";"Default contact" "BPARTNER";"Business partner";"CSLBPR";"Partner" "BPCARRIER";"Carriers";"BPTNUM";"Carrier" "BPCARRIER";"Carriers";"BPTNAM";"Company name" "BPCARRIER";"Carriers";"CNTNAM";"Default contact" "BPCCATEG";"Customer category";"REP";"Sales rep" "BPCCATEG";"Customer category";"REPDLV";"Sales rep" "BPCCATEG";"Customer category";"BPTNUM";"Carrier" …
Purge process
Purging rules are described in a metadata dictionary.
Each set of data (representing a document such as an order or an invoice) is described by a rule that includes the conditions that must be fulfilled to allow the purge of such data. These descriptions are supplied as standard but can be personalized to include additional rules. For example, you can define a dedicated status that prevents you from purging data automatically.
The purge parameters define the minimum storage duration for these documents.
The purge process can be launched per company or globally, in interactive mode or in batch mode.
- An alternative to purging master records is to obfuscate or blank personal data as soon as there is no legal, business, or contractual reason to keep it. Basic actions like removing emails, phone numbers, bank account numbers, or names is a simple and effective method that can also be considered.
- A manual deletion is also possible as long as no document references the master record. An additional feature described in the next paragraph gives you information about the document dates associated with a master record so that you can identify if you can delete the master record after purging such documents.
Personal data: List, content, and location
The standard data types and/or columns in tables associated with personal data main records are defined in a dictionary that is provided in standard but can be adapted to specific or vertical development. The settings are as follows:
Reference data type setup
Email data type setup
Phone column setup
Based on this setup, the following functions can retrieve and analyze personal data.
Personal data analysis: References to a master record
You can leverage all reporting tools delivered by the platform such as import/export templates, query tool, search engine, report designer, or additional tools like Business Intelligence platforms for data types identifying personal data.
From V11.0.8, GX V11.0.6, V12.0.14, HR V12.0.8, GX V12.0.19 and 2018 R3, a dedicated function helps you analyze these documents and find, for each master record, the date of the first and last document referencing it. You can decide which, if any, of these documents and their corresponding master records can be purged.
In addition, you can answer requests from individuals about the rights regarding their data.
The function runs in batch mode or in interactive mode, and is associated with a log file that can be opened as CSV file.
The page displays:
- The information to enter is the master key record (found using the search engine, for example).
- The first level grid lists the master data types for which a record has been found.
-
The second grid gives you the list of the first and last date of movement for each master record.
-
You can create a CSV file that can be opened with Excel.
Search engine
You could receive a request with limited details that make it difficult to identify the individual in your database. In this case, you can leverage all capabilities of the solution regarding data extraction, inquiries, and the query tool, including additional business intelligence tools connected to the solution.
As of V7.0, the solution includes a search engine and all personal data can be set as searchable to allow you to find the correct record to answer the request.
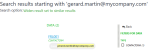
Starting with a name, you immediately find the associated records.
For example, if you search for Martin, you find several results that you can filter depending on what you are searching for: a CRM contact, a customer, an employee, or any other master record.
Searching for an email address would only give one result.
After the master record is found, you can use all the other tools to process the action needed.
Import/export data
The solution provides you with standard import/export templates associated with the different master records and documents. You can extract data to answer any data access request you receive.
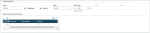
You can change the setup (shown below) to include additional fields. The output format can be ASCII with various separators (such as CSV), XML, or other formats.
Most templates, but not all of them, can be used for exports and imports. The consistency constraints of the solution need to be fulfilled.
This, in part, allows you to integrate data supplied by an individual (data portability).
Mailing prohibition
The solution provides standard checkboxes in contacts and prospects management that can help you uphold a mailing prohibition request sent by an individual person.
Data breach warning
If a data breach has been identified, you might need to contact the individuals directly to give them additional information. The solution provides you with tools to help in this process like the query tool and the import/export templates.
From V11.0.8, GX V11.0.6, V12.0.14, HR V12.0.8, GX V12.0.19 and 2018 R3, another feature extracts all the emails and phone numbers found in the database in a temporary table based on the related data type.
Access security and data filtering
You can manage user access to personal and sensitive data in the solution. We advise that you set up the security of your system according to best practices to limit the risk of data breaches and related penalties. You should also set up the security filters on data so that every user of the system has only the required access needed to perform their tasks.
The solution allows you to restrict each user’s access by function and to assign filtering rules to the corresponding data per company, site, access codes, or row-level permissions. An access code can be assigned to an individual record that globally restricts the ability to read, create, or perform complex operations on the record.
Access security is closely related to the audit features so you can manage access to sensitive or personal data.