How to secure mongoDB database
The mongoDB database can be accessed via different tools such as roboMongo. The access is done on a given port (27017 by default). For security reasons, it is recommended to secure this port against external connections.
From Update 9 and above, it is possible to secure the connection with a certificate and have high level security. But even before Update 9, securing the servers' port that runs mongoDB ensures very good security.
This document explains how to do this.
Mono-server configuration
The procedure is the following:
- Install mongoDB server, X3 and New Web server using standard procedures.
- Connect to New Web server, open Endpoints page, and select the “Syracuse Administration” endpoint.
- Make sure that the check box Use local database settings is checked.
- Identify the mongodb service configuration file. Depending on your setup, it could be mongod.cfg in mongodb program folder. Refer to your mongodb setup notes and service configuration.
- Add the parameter bind_ip=127.0.0.1 into the configuration file.
- Identify the web server’s configuration file : nodelocal.js located in Syracuse/bin folder.
- Modify the value config.collaboration.hostname to “localhost”
- Start mongodb
- Start Webserver
Cluster configuration
In a cluster configuration, mongoDB servers must access each other. The recommended configuration is to setup the firewalls to allow port 27017 to relevant servers only.
Reading mongoDB data from third party tools
Direct access to mongoDB from third party applications is not recommended. All data stored in mongoDB should be available through REST web services from Web server. This method guarantees services stability and user rights compliance.
Installing certificates (from release 9)
In release 9, the installation procedure of MongoDB can be done with certificates. In this case, using a tool like robomongo requires a dedicated setup that is summarized here:
- The installation procedure createS in the configuration directory (usually a
confsub-directory of the installation directory), a set of files related to certificates. The only file that you have to copy on the server that runs 'robomongo' is calledclient.pem. This file can be renamed. - When launching 'robomongo', the configuration setup has to be defined as shown in the screen:
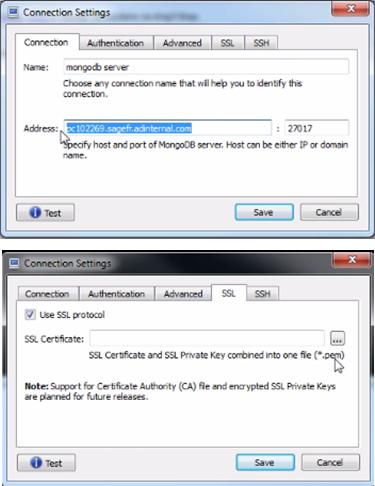
- The address of the MongoDB server must be the full qualified name.
- The Use SSL protocol checkbox must be set.
- The SSL certificate entered must be the
client.pemfile previously copied/renamed.
